04N01 Sicherheit von lokalen Netzen
|
IT-Netze sind der Lebensnerv des Unternehmens. Verfügbarkeit und Sicherheit der Netze müssen durch angemessene Konzeption und adäquate technische Maßnahmen sichergestellt werden. Dieser Beitrag stellt nachvollziehbare Prinzipien und praxiserprobte Umsetzungen vor, die optimale Verfügbarkeit und Sicherheit vor Fehlern und Angriffen zum Ziele haben. Zu einer guten Umsetzung gehört die angemessene Dokumentation.
Es wird gezeigt, nach welcher Systematik Sie eine angemessene Dokumentation aufbauen können und wie diese Dokumentation ein Weg zu zertifizierbarer Sicherheit wird. Arbeitshilfen: von: |
1 Unternehmensnetze
Netzwerksicherheit ist ein Zustand der bestmöglichen Betriebssicherheit der IT-Netze eines Unternehmens. Die Betriebssicherheit wird ergänzt um den Schutz vor individuellen Bedrohungen der Unternehmenswerte, die durch die IT-Netze nutzbar gemacht werden.
Nicht nur Technik
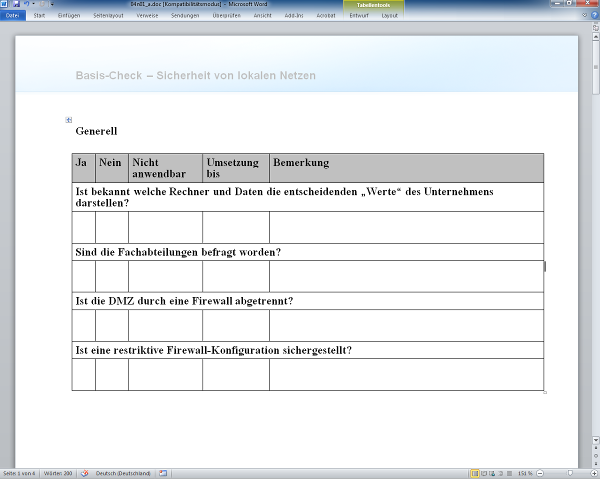
Netzwerksicherheit wird in vielen Unternehmen ganz einseitig technisch betrachtet. Der Aufbau einer Firewall und der Einsatz von Antivirensoftware sind sicherlich unbedingt nötig. Solche Maßnahmen sind aber nur die abschließenden und sichtbaren Umsetzungen einer umfassenden IT-Sicherheits-Strategie.
Netzwerksicherheit wird in vielen Unternehmen ganz einseitig technisch betrachtet. Der Aufbau einer Firewall und der Einsatz von Antivirensoftware sind sicherlich unbedingt nötig. Solche Maßnahmen sind aber nur die abschließenden und sichtbaren Umsetzungen einer umfassenden IT-Sicherheits-Strategie.
Sicherheit ist überwiegend ein organisatorisches, erst nachrangig ein technisches Problem. Voraussetzung für das Erreichen und Halten eines angemessenen Sicherheitsniveaus ist eine klare, möglichst einfach strukturierte Organisation der IT-Sicherheit.