03245 Information Security Management
|
Die Prozesse, Verfahren und Richtlinien für ein Information Security Management System (ISMS) müssen in verbindlicher und verständlicher Form allen Beteiligten bekannt gegeben werden und nachvollziehbar sein. Dies erfordert u. a. eine Dokumentation der Vorgaben, die diesen Ansprüchen gerecht wird.
Der Beitrag zeigt auf, welche Anforderungen an eine ISMS-Dokumentation zu stellen sind und wie diese Anforderungen durch eine geeignete Dokumentationsrichtlinie erfüllt werden können. Beispiele für eine Dokumentenstruktur erläutern die Vorgaben. Arbeitshilfen: von: |
1 Notwendigkeit einer angemessenen Dokumentation
Besonders in einem Information Security Management System (ISMS) ist es von hoher Bedeutung, dass wichtige Prozesse, Abläufe, Richtlinien usw. im Unternehmen verbindlich festgelegt, vermittelt und angewendet werden.
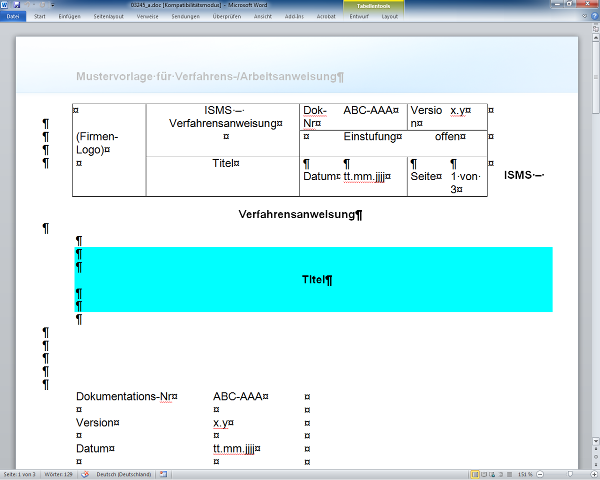
Verfahren festlegen
In vielen Fällen bietet es sich an, solche „Festlegungen” als Verfahrens- oder Arbeitsanweisungen zu dokumentieren, wie man diese Art der Dokumentation bereits seit vielen Jahren in der Welt der Qualitätsmanagementsysteme (siehe ISO 9001) und Umweltschutzmanagementsysteme (siehe ISO 14001) kennt.
In vielen Fällen bietet es sich an, solche „Festlegungen” als Verfahrens- oder Arbeitsanweisungen zu dokumentieren, wie man diese Art der Dokumentation bereits seit vielen Jahren in der Welt der Qualitätsmanagementsysteme (siehe ISO 9001) und Umweltschutzmanagementsysteme (siehe ISO 14001) kennt.
Durch Beratungs- und Zertifizierungsunternehmen wurde festgestellt, dass fehlende oder unzureichende Dokumentation eine der am häufigsten festgestellten Abweichungen von der Anforderung der DIN EN ISO 27001 ist. Die Gründe hierfür sind vielfältiger Natur. Ein Grund ist sicherlich die fehlende Erfahrung der Mitarbeiter in der Erstellung von derartigen Dokumenten. Dies trifft insbesondere für kleinere und mittelständische Unternehmen zu, die zudem aufgrund der Firmengröße und -struktur keinen nennenswerten Aufwand für Dokumentation wünschen (Zitat: „Wir kamen bisher doch auch ohne Dokumentation aus”).