03110 Information Security – eine unternehmerische Aufgabe
|
Das eigene Unternehmen erfolgreich zu machen und seine Zukunft zu sichern sind ureigene Aufgaben der Geschäftsleitung. Sie muss Chancen identifizieren und wahrnehmen. Den Chancen des Unternehmens stehen jedoch auch Risiken gegenüber. Sie durch wirtschaftlich angemessene organisatorische Regelungen und technische Maßnahmen auf das u. a. schon gesetzlich geforderte Niveau zu bringen, liegt in der Verantwortung der Unternehmensleitung.
Der Beitrag geht ein auf interne Anforderungen sowie auf externe von Stakeholdern wie z. B. Gesetzgeber, Aufsichtsbehörden, Wirtschaftsprüfern und Normungsgremien sowie auf das Thema Gesetzeskonformität, also Compliance. Er spricht Chancen des Unternehmens und der IT-Nutzung ebenso an wie Unternehmensrisiken und die Haftungsrisiken von Personen, die mit der Unternehmensleitung betraut sind. Die vitale Bedeutung von Informationen und ihrer Verarbeitung erfordert ein effizientes und zielgerichtetes Informationssicherheitsmanagement (ISM) zur Reduzierung der Risiken. Der Beitrag behandelt außerdem die Vorgehensweise zum Aufbau des Information Security Management und geht ein auf organisatorische, technische und personelle Aspekte der Informationssicherheit. Arbeitshilfen: von: |
1 Informationssicherheit – strategische Aufgabe des Managements
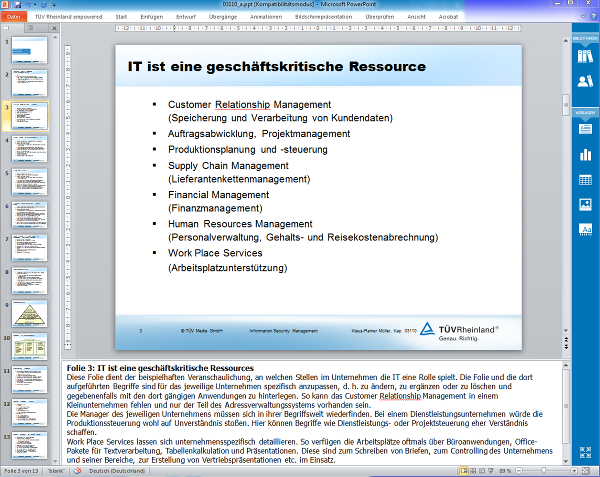
Unternehmenserfolg sichern
Wirtschaftlicher Erfolg und Zukunftssicherung des eigenen Unternehmens sind Kernaufgaben der Unternehmensleitung. Unternehmensziele sollen erreicht, Chancen ergriffen und zu hohe Risiken durch angemessene Schutzmaßnahmen effizient reduziert werden. Gleichzeitig sollen Gewinne und die Wirtschaftlichkeit gesteigert werden. Um dies zu erreichen, automatisieren Unternehmen ihre Prozesse, verlagern Aufgaben auf Kunden, lagern Services an Dienstleister aus und setzen nicht zuletzt die Informationstechnologie (IT) ein.
Wirtschaftlicher Erfolg und Zukunftssicherung des eigenen Unternehmens sind Kernaufgaben der Unternehmensleitung. Unternehmensziele sollen erreicht, Chancen ergriffen und zu hohe Risiken durch angemessene Schutzmaßnahmen effizient reduziert werden. Gleichzeitig sollen Gewinne und die Wirtschaftlichkeit gesteigert werden. Um dies zu erreichen, automatisieren Unternehmen ihre Prozesse, verlagern Aufgaben auf Kunden, lagern Services an Dienstleister aus und setzen nicht zuletzt die Informationstechnologie (IT) ein.
Bedohungen und Risiken nehmen zu
Gleichzeitig gilt es dabei Rahmenbedingungen zu berücksichtigen: Bedrohungen für Unternehmen und insbesondere für deren IT nehmen rasant zu. Immer größere und neue erfolgreiche Attacken zeigen dies. Zudem können Angreifer kritische Infrastrukturen wie die Stromversorgung lahmlegen und manches Unternehmen, das von diesen abhängig ist, handlungsunfähig machen – selbst bei überschaubarer Dauer des Ausfalls. Diese Angreifer können Einzeltäter sein, aber auch die organisierte Kriminalität, Terroristen und sogar Geheimdienste oder Militärs.
Gleichzeitig gilt es dabei Rahmenbedingungen zu berücksichtigen: Bedrohungen für Unternehmen und insbesondere für deren IT nehmen rasant zu. Immer größere und neue erfolgreiche Attacken zeigen dies. Zudem können Angreifer kritische Infrastrukturen wie die Stromversorgung lahmlegen und manches Unternehmen, das von diesen abhängig ist, handlungsunfähig machen – selbst bei überschaubarer Dauer des Ausfalls. Diese Angreifer können Einzeltäter sein, aber auch die organisierte Kriminalität, Terroristen und sogar Geheimdienste oder Militärs.
Ferner erpressen organisierte Computerkriminelle Unternehmen immer häufiger, nachdem sie deren IT blockiert haben. Dazu verschlüsseln sie z. B. deren Daten und machen so ihre Nutzung unmöglich. In einer anderen Erpressungsvariante blockieren sie Onlinedienste, indem sie diese mit Nachrichten bombardieren, bis sie vom Netz genommen werden müssen.