03720 Security Event Management
|
Die regelmäßige Auswertung von IT-Systemlogs im Rahmen eines Security-Event-Management-Ansatzes (SEM) kann wertvolle Hinweise auf Angriffsversuche und missbräuchliche Verwendung oder auch auf fehlerhafte Systemkonfigurationen liefern. Gleichzeitig fordern gesetzliche und aufsichtsrechtliche Bestimmungen eine angemessene Überwachung der Unternehmens-IT und damit ggf. auch Überprüfungen der Systemlogs.
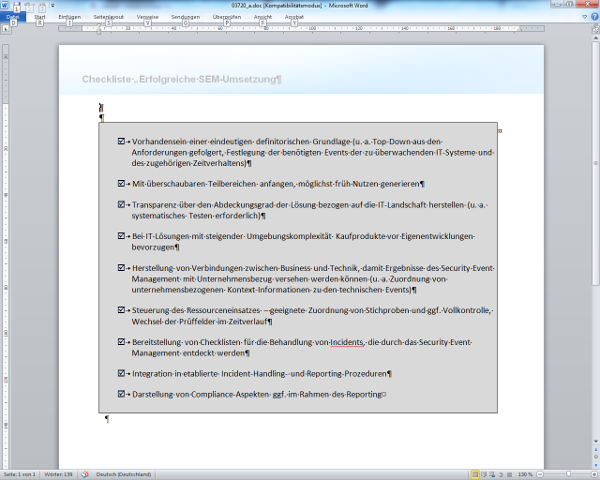
Dieser Beitrag stellt ein strukturiertes, schrittweises Vorgehen für die Etablierung eines Security Event Management vor, das den individuellen Anforderungen und Zielsetzungen des Unternehmens Rechnung trägt, früh zu verwertbaren Ergebnissen führt und an zukünftige Anforderungen angepasst werden kann. Aufbauend auf strategischen und methodischen Aspekten werden detaillierte Umsetzungshinweise für die einzelnen Schritte in der Praxis gegeben sowie Schnittstellen zu angrenzenden Themengebieten wie Incident Handling dargestellt. Eine Betrachtung der grundsätzlichen Architektur von SEM-Systemen, Hinweise für eine IT-Lösungsauswahl und ein Fazit mit zusammenfassenden Tipps für die Praxis schließen den Beitrag ab. Arbeitshilfen: von: |
1 Motivation und aktuelle Anforderungen
Ausgangssituation
Aufgrund bestehender gesetzlicher und regulatorischer Anforderungen ist eine angemessene Überwachung von IT-Systemen für immer mehr Unternehmen inzwischen erforderlich („Compliance”). Dies umfasst ggf. auch die regelmäßige Auswertung von Protokollen.
Aufgrund bestehender gesetzlicher und regulatorischer Anforderungen ist eine angemessene Überwachung von IT-Systemen für immer mehr Unternehmen inzwischen erforderlich („Compliance”). Dies umfasst ggf. auch die regelmäßige Auswertung von Protokollen.
Aber auch zur Kontrolle und Beobachtung des Sicherheitsstatus werden Protokolle immer wichtiger. Denn die in Protokolldateien bzw. Logs von IT-Systemen enthaltenen Daten können in hohem Maße sicherheitsrelevante Informationen enthalten. Dies umfasst unter anderem Indikatoren für missbräuchliche Verwendung, Hinweise auf Angriffsversuche oder auch Auswirkungen von fehlerhaften Systemkonfigurationen.
Mögliche Fragen
Auf der Basis von geeigneten Log-Auswertungen lassen sich dann z. B. Fragen wie diese beantworten:
Auf der Basis von geeigneten Log-Auswertungen lassen sich dann z. B. Fragen wie diese beantworten: